
Privileged Access Management (PAM)

Protect your organization's digital environment and effectively achieve Zero Trust goals by implementing Privileged Access Management workflows to minimize cyber risks.

Trusted by
Incorporate Zero Trust Principles
into Privileged Access Management
Resource Reservation
Thinfinity’s Resource Reservation Module streamlines the process of providing temporary remote application access to employees, contractors, and vendors. With an easy-to-use interface, it allows for the swift setup and approval of temporary access privileges, enhancing security and efficiency. This approach aligns with Zero Trust principles by ensuring that access is securely managed and granted on a need-to-use basis.
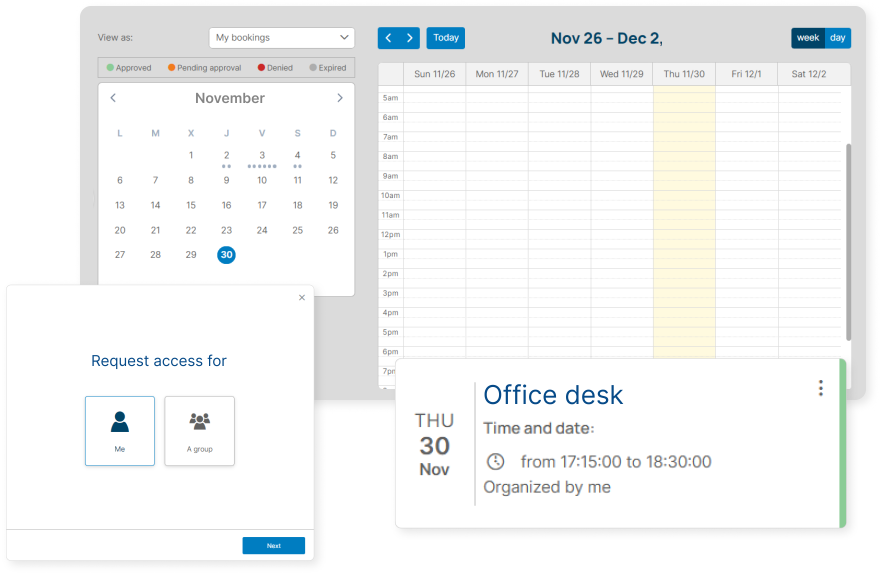
Streamline Processes with Thinfinity's Approval Workflows
Automated Approval Requests
Facilitates quick and efficient handling of access requests with automated workflow mechanisms.
Customizable Workflow Design
Provides the capability to customize approval workflows to align with unique organizational requirements and access policies, accommodating various role types such as administrators, users, and supervisors.
Multi-Level Approval System
Supports complex, multi-tiered approval processes for enhanced security and control over access permissions.
Real-Time Notifications
Keeps relevant parties informed with instant notifications in portal and by email on approval requests and decisions.
Audit Trail and Compliance
Ensures a complete audit trail of approvals for compliance purposes, providing transparency and accountability in access management.
Use Cases
Temporary and time based access for Employees
Incorporates efficient approval processes for temporary access requests, ensuring quick and secure authentication.
Enables precise, time-limited access permissions for temporary employees, aligning with short-term project needs and enhancing security.
Adheres strictly to least privilege access, granting temporary employees only the necessary rights to perform their specific job functions.
Offers compatibility with multiple Identity Providers (IDPs), ensuring seamless integration with various external authentication systems.
Includes robust monitoring and detailed audit logs, offering complete visibility and tracking of temporary employee activities and access patterns.
Vendor Privileged Access Management (VPAM)
VPAM enables secure vendor access to your organization's assets, extending best practices of privileged access security beyond the perimeter.
Features an intuitive system for authorizing reservation requests and managing vendor access, aligning with your organizational workflow needs.
Utilize a flexible permission structure to create custom roles for vendors, tailored to specific access and operational requirements.
Managed credentials are directly injected for remote sessions, ensuring vendors never receive actual passwords, enhancing both security and operational efficiency.
Access is limited to the bare minimum required, with an emphasis on just-in-time access models to prevent excessive or persistent vendor privileges.
Secure access to Cloud Infrastructure
Introduces easy-to-navigate approval processes for secure connectivity, enhancing cloud developer and DevOps engineer productivity.
Offers seamless and secure access solutions, tailored for diverse cloud infrastructures.
Implements advanced authentication mechanisms, ensuring secure and reliable access for all cloud-based operations.
Features extensive auditing tools, providing transparent and detailed insights into access and usage across cloud environments.
Specifically designed to support the unique demands of cloud infrastructure, facilitating smooth, secure operations for developers and engineers.
Core Features
Preferred by teams globally for ensuring secure access
Thinfinity enables secure, fluid connections to IT frameworks, cloud services, and OT systems from any location, avoiding the need for VPNs enhancing security and seamless access.
Gain full control over privileged sessions with detailed tracking and documentation, ensuring effortless compliance and secure oversight.
Implement least privilege and just-in-time access, providing users with necessary remote access for the exact duration needed, optimizing security.
Monitor privileged activities in real-time with an advanced system that alerts administrators to unusual activities, enhancing security response.
Incorporate multi-factor, passwordless, and SAML authentications for efficient, secure system access, improving user experience and security.
Achieve SOC 2 compliance with in-depth session audits and analytics, offering immediate and historical insights for robust security management.
Product Highlights
Zero Trust Architecture (ZTA)
Expand Privileged Access Management (PAM) best practices to encompass remote access. Aligned with zero trust principles, Thinfinity’s solution ensures that all access across the enterprise is justified, properly scaled, and meticulously documented. It allows for just-in-time access tailored for internal teams, external vendors, and OT systems, using detailed least privilege access controls.
Simplify Access for End Users
Privileged Remote Access enables a smooth user experience that empowers users to work with the tools they want.
By brokering all connections through a single, secure access pathway, your attack surface is significantly reduced. Oversight and auditing are also simplified by getting a single list of authorized endpoints available for each user.
Gain Complete Oversight Over Privileged Sessions
Streamline remote session management using Thinfinity’s centralized platform, compatible with a wide array of protocols: RDP, VNC, HTTPS, SSH, SQL, Webdav, WAG, TN3250, TN5250, Thinfinity VNC, and VirtualUI. Administrators have complete control over session scheduling, user access, and application permissions, along with the ability to capture and review session data.
Let’s connect
We want to hear about your challenges and help you achieve your goals.
Talk to us, we’re listening.